Google: OAuth2 generic#
This document contains instructions for creating a generic OAuth2 Google credential for use with custom operations.
Prerequisites#
- Google Cloud account
- Google Cloud Platform project
- If you haven't used OAuth in your Google Cloud project before, you need to configure the OAuth consent screen.
- If using Google Perspective: Request API Access
- If using Google Ads: Developer Token
Set up OAuth#
Create a new credential in n8n#
- Follow the steps to Create a credential. If you create a credential by selecting Create new in the credentials dropdown in a node, n8n automatically creates the correct credential type for that node. If you select Credentials > New, you must browse for the credential type. To create a credential for a custom API call, select Google OAuth2 API. This allows you to create a generic credential, then set its scopes.
-
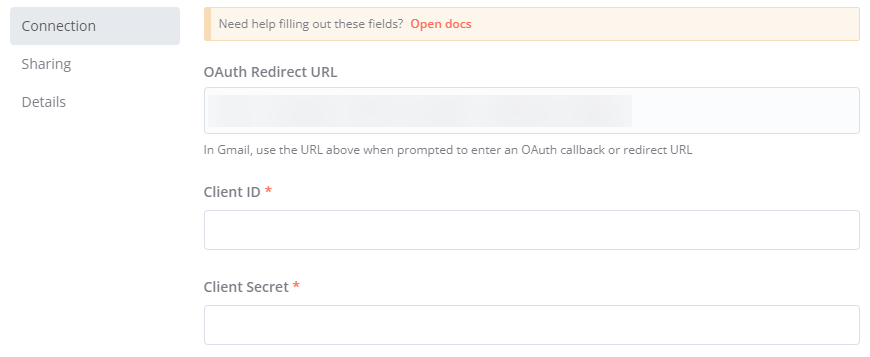
Note the OAuth Redirect URL from the node credential modal. You'll need this in the next section.
View screenshot
-
You must provide the scopes for this credential. Refer to Scopes for more information.
Set up OAuth in Google Cloud#
-
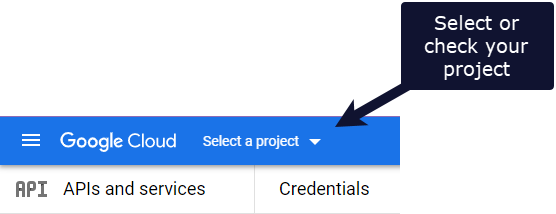
Go to Google Cloud Console and make sure you're in the project you want to use.
View screenshot
-
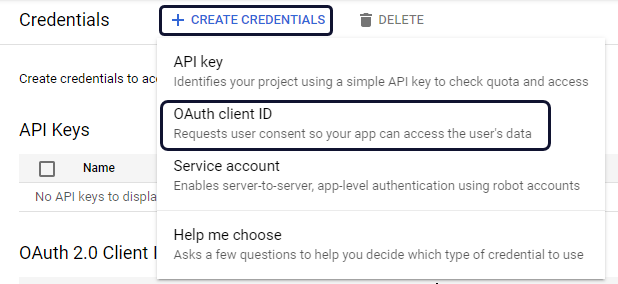
Select + CREATE CREDENTIALS > OAuth client ID. .
View screenshot
-
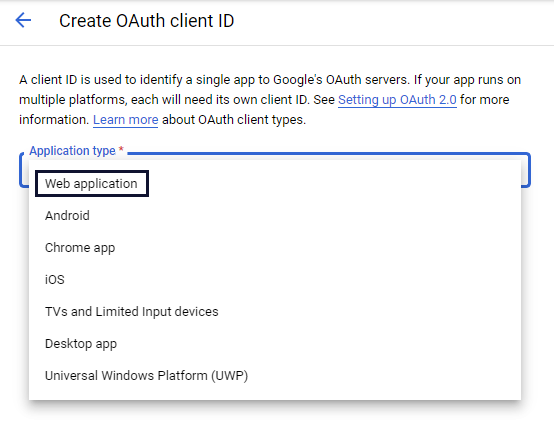
In the Application type dropdown, select Web application. Google automatically generates a name.
-
Under Authorizes redirect URIs, select + ADD URI. Paste in the OAuth redirect URL from the previous step.
View screenshot
-
Select CREATE.
- Enable each Google service API that you want to use:
- Access your Google Cloud Console - Library. Make sure you're in the correct project.
- Search for and select the API(s) you want to enable. For example, for the Gmail node, search for and enable the Gmail API.
- Select ENABLE.
Create and test your connection#
In n8n:
- Enter your new Client ID and Client Secret from Google Cloud Console in the credentials modal.
- Select Sign in with Google to complete your Google authentication.
- Save your new credentials.
The following video demonstrates the steps described above:
Scopes#
Many Google services have multiple possible access scopes. A scope limits what a user can do. Refer to OAuth 2.0 Scopes for Google APIs for a list of scopes for all services.
n8n doesn't support all scopes. When creating a generic Google OAuth2 API credential, you can enter scopes from the list. If you enter a scope that n8n doesn't already support, it won't work.
Supported scopes
| Service | Available scopes |
|---|---|
| Gmail | https://www.googleapis.com/auth/gmail.labels https://www.googleapis.com/auth/gmail.addons.current.action.compose https://www.googleapis.com/auth/gmail.addons.current.message.action https://mail.google.com/ https://www.googleapis.com/auth/gmail.modify https://www.googleapis.com/auth/gmail.compose |
| Google Ads | https://www.googleapis.com/auth/adwords |
| Google Analytics | https://www.googleapis.com/auth/analytics https://www.googleapis.com/auth/analytics.readonly |
| Google Big Query | https://www.googleapis.com/auth/bigquery |
| Google Books | https://www.googleapis.com/auth/books |
| Google Calendar | https://www.googleapis.com/auth/calendar https://www.googleapis.com/auth/calendar.events |
| Google Cloud Natural Language | https://www.googleapis.com/auth/cloud-language https://www.googleapis.com/auth/cloud-platform |
| Google Cloud Storage | https://www.googleapis.com/auth/cloud-platform https://www.googleapis.com/auth/cloud-platform.read-only https://www.googleapis.com/auth/devstorage.full_control https://www.googleapis.com/auth/devstorage.read_only https://www.googleapis.com/auth/devstorage.read_write |
| Google Contacts | https://www.googleapis.com/auth/contacts |
| Google Docs | https://www.googleapis.com/auth/documents https://www.googleapis.com/auth/drive https://www.googleapis.com/auth/drive.file |
| Google Drive | https://www.googleapis.com/auth/drive https://www.googleapis.com/auth/drive.appdata https://www.googleapis.com/auth/drive.photos.readonly |
| Google Firebase Cloud Firestore | https://www.googleapis.com/auth/datastore https://www.googleapis.com/auth/firebase |
| Google Firebase Realtime Database | https://www.googleapis.com/auth/userinfo.email https://www.googleapis.com/auth/firebase.database https://www.googleapis.com/auth/firebase |
| Google Perspective | https://www.googleapis.com/auth/userinfo.email |
| Google Sheets | https://www.googleapis.com/auth/drive.file https://www.googleapis.com/auth/spreadsheets |
| Google Slide | https://www.googleapis.com/auth/drive.file https://www.googleapis.com/auth/presentations |
| Google Tasks | https://www.googleapis.com/auth/tasks |
| Google Translate | https://www.googleapis.com/auth/cloud-translation |
| GSuite Admin | https://www.googleapis.com/auth/admin.directory.group https://www.googleapis.com/auth/admin.directory.user https://www.googleapis.com/auth/admin.directory.domain.readonly https://www.googleapis.com/auth/admin.directory.userschema.readonly |
Troubleshooting#
Google hasn't verified this app#
If using the OAuth authentication method, you might see the warning Google hasn't verified this app. To avoid this, you can create OAuth credentials from the same account you want to authenticate. However, if you're using credentials that were generated by another account (by a developer or another third party), do the following in Google Cloud:
- SelectAdvanced.
- Select Go to CREDENTIALS_NAME (unsafe).
CREDENTIALS_NAMEis the name of the credentials created by the third party. - Grant the requested permissions.